Microsoft Intune Connector for Active Directory Security Update: A Safer Way to Hybrid Join
Picture this: you're managing a hybrid environment, juggling Microsoft Intune and Active Directory like a circus performer with flaming torches. Everything’s going fine until you hear about a security update for the Intune Connector for Active Directory. Suddenly, your torches feel a bit heavier. Fear not! Microsoft’s latest update to the Intune Connector is here to make your hybrid deployments more secure, less privileged, and dare I say, a little less stressful. Let’s dive into what’s changing, why it’s a better way, and how to configure this shiny new connector with a Managed Service Account (MSA). Buckle up, it’s time to tame the hybrid beast
What’s Changing?
The Intune Connector for Active Directory, the unsung hero behind Microsoft Entra hybrid-joined devices, is getting a security glow-up. Previously, the connector ran under the local SYSTEM account, which, let’s be honest, had more privileges than a VIP at an all-you-can-eat buffet. This over-privileged setup could potentially be exploited, making your environment a bit too exciting for comfort.
As of February 27, 2025, Microsoft has released a new version of the Intune Connector that swaps the SYSTEM account for a Managed Service Account (MSA). This change reduces unnecessary permissions, tightens security, and ensures that your hybrid join process is as locked down as a bank vault. Oh, and here’s the kicker: older versions using the SYSTEM account will stop working after July 1, 2025 (originally planned for May, but Microsoft gave us a bit of breathing room). So, it’s time to upgrade, or your hybrid deployments might throw a tantrum.
Why Is This a Better Way?
Using a Managed Service Account is like giving your Intune Connector a tailored suit instead of a one-size-fits-all poncho. Here’s why it’s a game-changer:
- Reduced Privileges: The MSA operates with the least privilege necessary, meaning it only has the permissions it needs to get the job done. No more handing out admin-level access like free candy on Halloween.
- Enhanced Security: By minimizing the attack surface, the MSA reduces the risk of exploitation. It’s like putting a deadbolt on your front door instead of leaving it wide open.
- Simplified Management: MSAs handle their own password management and rotation, so you don’t have to play password babysitter. This frees you up to focus on more pressing tasks, like figuring out why Bob from accounting keeps clicking phishing links.
- Future-Proofing: With Microsoft tightening the screws on security, adopting the MSA now ensures your environment stays compliant and ready for whatever comes next.
In short, the MSA makes your Intune Connector leaner, meaner, and a whole lot safer. It’s the IT equivalent of swapping a rusty old bike for a sleek, secure electric scooter.
What Is a Managed Service Account (MSA)?
For those wondering, “What’s this MSA thing everyone’s talking about?”—let me break it down. A Managed Service Account is a special type of Active Directory account designed for services and applications. Unlike a regular user account, an MSA is managed by Active Directory itself, which takes care of password updates and security configurations. Think of it as a low-maintenance pet: it does its job, doesn’t need constant feeding, and won’t chew up your network’s security.
MSAs are tied to a specific computer, have automatic password rotation, and can be granted just the permissions needed for their role—in this case, helping the Intune Connector facilitate hybrid joins. It’s like hiring a highly specialized intern who never forgets their password and doesn’t need coffee breaks.
Comparing the account permissions required between the new and old connector

Step-by-Step Configuration
🔥 Step 1: Uninstall the Old Connector
1.1 Uninstall via Windows Settings
- Open the Settings app.
- Go to Apps > Installed Apps.
- Find Intune Connector for Active Directory.
- Click Uninstall.
1.2 Use the ODJConnectorBootstrapper.exe
- Run
ODJConnectorBootstrapper.exe. (Installation file) - Choose Uninstall.
- Confirm and let it do its thing.
📦 Step 2: Meet the Minimum Requirements
Before installing the new connector, make sure your environment is ready. Think of this as the pre-flight checklist:
🧱 Infrastructure Requirements
- .NET Framework 4.7.2 or later
- Windows Server with 2008 R2 functional level (or newer)
- Local administrator permissions on the server
👤 Account Requirements
- Microsoft Entra account with atleast:
- Intune Service Administrator permissions
- Intune license assigned
- Domain account with:
- Local administrator privileges
- Permission to create
msDS-ManagedServiceAccountobjects in Active Directory
⬇️ Step 3: Download the New Connector
- Go to the Microsoft Intune Admin Center.
- Navigate to Devices > Enrollment > Intune Connector for Active Directory.
- Click Add and download the latest connector build. (make sure the version is greater than or equal to 6.2501.2000.5)
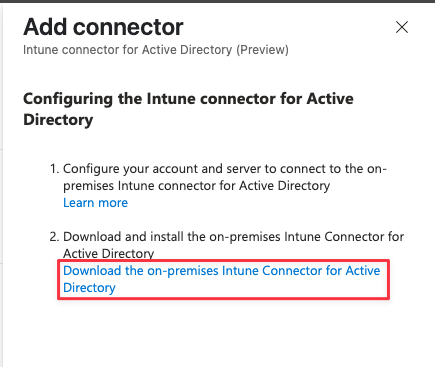
🛠️ Step 4: Install the New Connector
4.1 Run the Installer
- Double-click the installer.
- Follow the prompts.
- When asked to sign in, use your Microsoft Entra account with the right permissions.
After signing in, the connector will enroll and only the Configure Managed Service Account option will be available
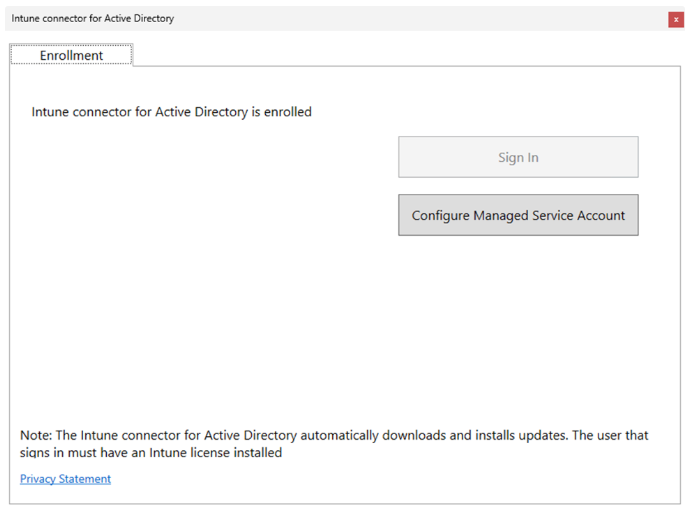
By default, MSAs don’t have access to create computer objects in any OU. If you wish to use a custom OU for domain join, you’ll need to update the ODJConnectorEnrollmentWiazard.exe.config file. This can be done at any time (either before enrollment, or after the connector is enrolled):
Update ODJConnectorEnrollmentWizard.exe.config:
- Default location is “C:\Program Files\Microsoft\Intune\ODJConnector\ODJConnectorEnrollmentWizard”
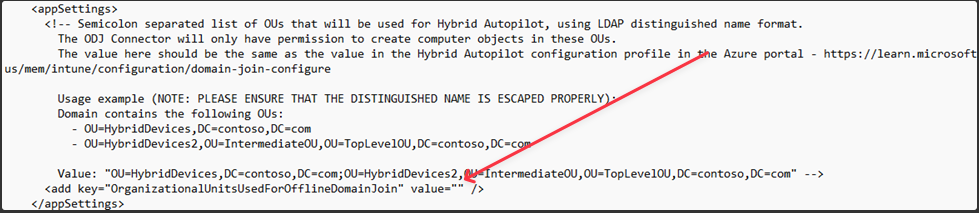
- In the
add keyelement of theODJConnectorEnrollmentWizard.exe.configXML file: Add all the OUs required in OrganizationalUnitsUsedForOfflineDomainJoin - OU name should be the distinguished name (see Additional information section at the bottom of this page)
- example:
OU=HybridDevice,DC=Contoso,DC=local
- example:
Note that the MSA is only granted access to the OUs configured in this file (and the default Computers container). If any OUs are removed from this list, completing the rest of the steps will revoke access.
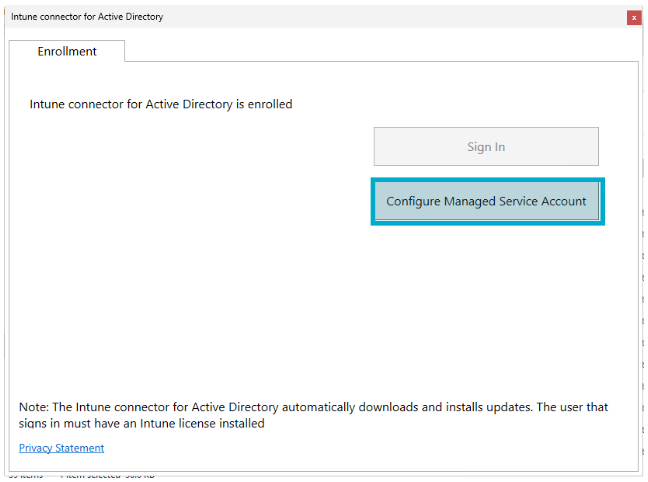
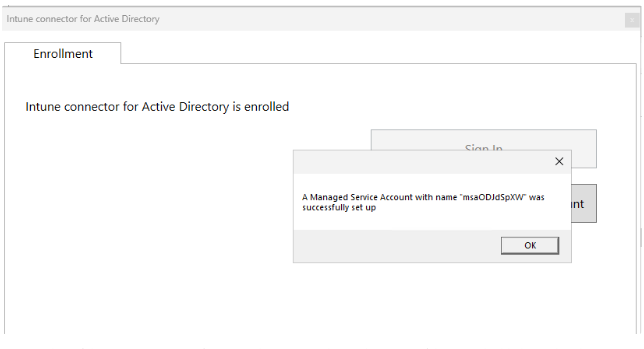
- Open ODJConnectorEnrollmentWizard (or restart it if it was open) and select the “Configure Managed Service Account” button.
- Success! – A pop up will appear showing success.
After the Intune Connector for Active Directory is installed, it will start logging in the Event Viewer under the path Applications and Services Logs > Microsoft > Intune > ODJConnectorService. Under this path, Admin and Operational logs can be found.
Additional information
Retrieving Organizational Unit Distinguished Name
Active Directory Users and Computers
- Select “View” from the menu, and enable “Advanced Features”
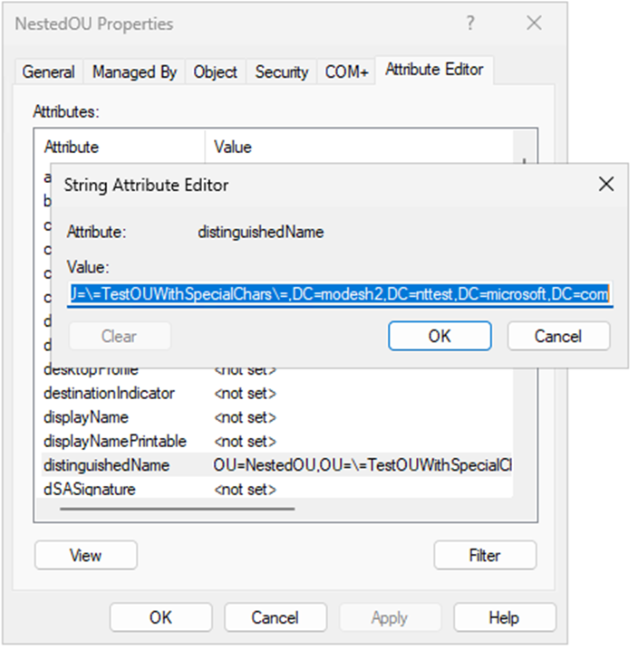
- Right click on the specific OU and click “Properties”
- Navigate to the “Attribute Editor” tab
- Select “distinguishedName” attribute and click “View”
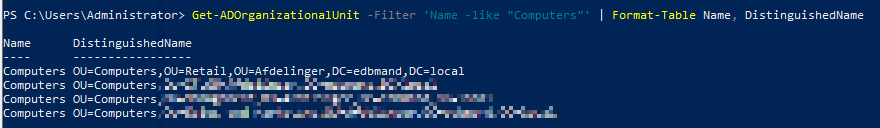
Powershell
Retrieve Distinguishedname with Powerhshell
Get-ADOrganizationalUnit -Filter 'Name -like "YourOu"' | Format-Table Name, DistinguishedName
Wrapping Up
The updated Intune Connector for Active Directory is like giving your hybrid environment a security shield and a cape. By moving to a Managed Service Account, Microsoft ensures your connector is secure, efficient, and ready for the future—all without making you play password manager. Don’t wait until the July 1, 2025, deadline to upgrade. Get that new connector installed and configured now, and keep your hybrid joins running smoother than a sunny day at the IT circus.
For more details, check out Microsoft’s official blog post: Microsoft Intune Connector for Active Directory Security Update.
Now, go make those hybrid devices shine!
