Microsoft Entra Global Secure Access Multi-Geo Public Preview
Microsoft has just rolled out the public preview of Multi-Geo support for Microsoft Entra Private Access, a game-changer for organizations with a global footprint. This feature allows businesses to route network traffic through specific geographic regions, ensuring compliance with data residency requirements, optimizing performance, and enhancing security. Whether you’re a multinational corporation or a company with remote workers across continents, Multi-Geo support empowers you to tailor your network access strategy to meet regional needs while maintaining a Zero Trust security model.
Why Multi-Geo Matters
Multi-Geo support in Global Secure Access addresses key challenges for global organizations:
- Data Residency Compliance: Route traffic through specific regions to meet local regulations, ensuring sensitive data stays within designated geographies.
- Optimized Performance: Connect users to the closest Microsoft network edge, reducing latency and improving app performance.
- Granular Control: Assign users or groups to specific regions for tailored access policies, enhancing security and user experience.
This preview strengthens Microsoft’s Security Service Edge (SSE) solution, focusing on Microsoft Entra Private Access to secure connections to private resources from anywhere. With Multi-Geo, you can now align your private network strategy with your organization’s global operations.
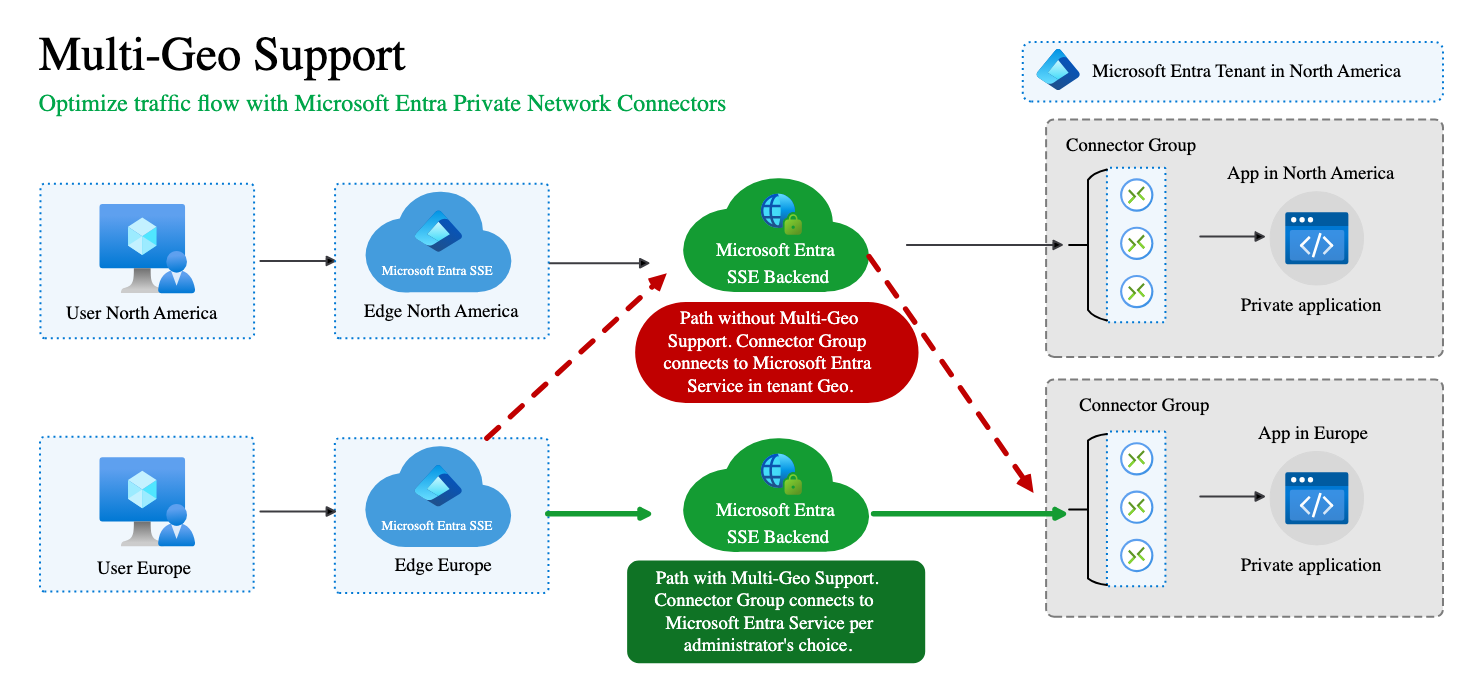
Multi-Geo capability helps optimize traffic flow from Microsoft Entra clients to Microsoft Entra apps through private access. Currently, the tenant's default geo location determines the Microsoft Entra routing for private access. For instance, if a tenant's default region is North America, all connector groups must connect to the Microsoft Entra backend in North America, even if some applications and connector groups are in different regions. Multi-Geo support lets customers optimize traffic flow by assigning connector groups according to their preferred geo locations instead of relying solely on the tenant's geo location. Each connector group connects to the SSE backend in the selected area, enhancing overall efficiency. This arrangement provides you with the flexibility to direct connections to the SSE backend of choice.
Step-by-Step Guide: Setting Up Multi-Geo in Microsoft Entra Private Access
Follow this guide to configure Multi-Geo support, as outlined in the official documentation.
Prerequisites
Before you begin, ensure you have:
- A Microsoft Entra tenant onboarded to Private Access.
- Global Secure Access Administrator or Global Administrator role.
- Appropriate licensing for Private Access (check licensing details in the Microsoft Entra admin center).
- The Global Secure Access client installed on end-user devices (Windows, macOS, iOS, or Android).
Step 1: Sign in to the Microsoft Entra Admin Center
- Open a web browser and navigate to the Microsoft Entra admin center.
- Sign in with an account that has Global Secure Access Administrator or Global Administrator permissions.
Step 2: Creating Connector Groups
- Browse to Applications > Enterprise applications > Your Application > Private Network connectors.
- Create two connector groups, each associated with a different geographic region.
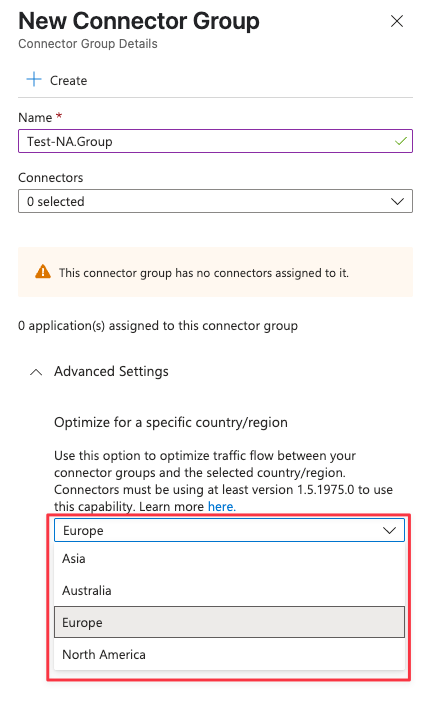
- Select + New Connector Group.
- In the New Connector Group pane, enter a name for the connector group.
- Under Advanced settings, select the optimized country/region for the connector group. The region you select determines the backend that the connector group connects to.
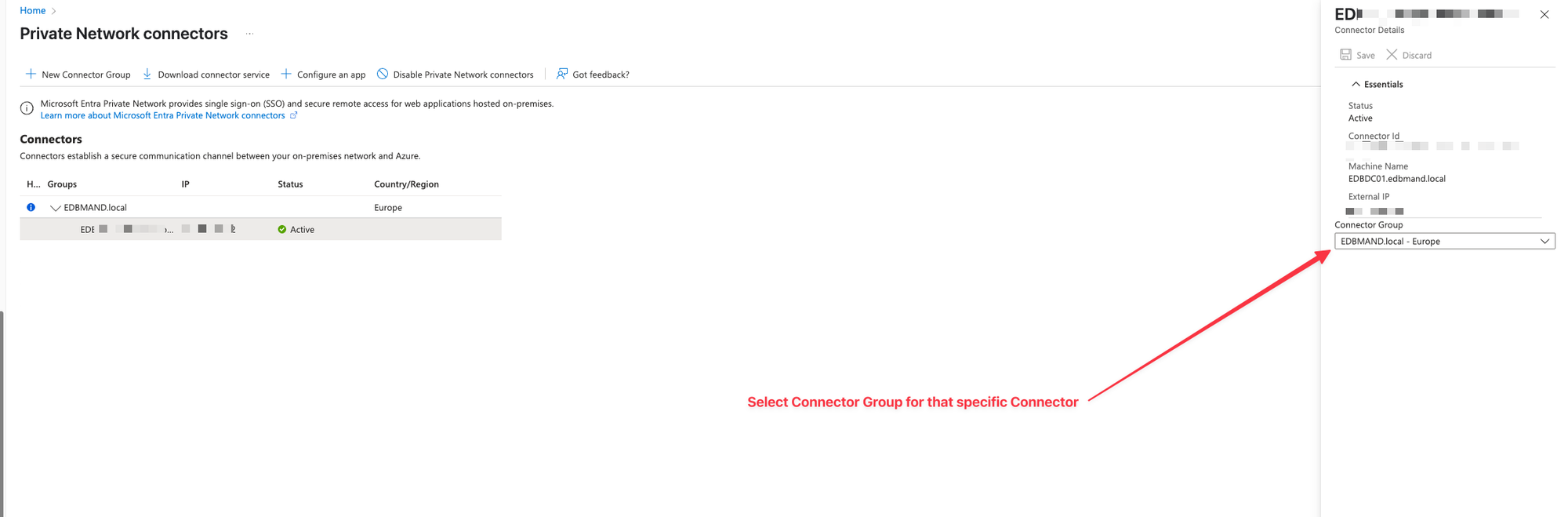
Install a connector in each region or move existing connectors to the new Connector Groups. For more information, see How to configure private network connectors for Microsoft Entra Private Access and Microsoft Entra application proxy.
- Add an application segment to each of the connector groups.
- Browse to Global Secure Access > Applications > Enterprise applications > Your Application > Network access properties.
- Select + Add application segment.
- Select the application segment you want to add to the connector group.
- Select Save.
- Repeat steps a - d for the second connector group.
- After about 30 minutes, the multi-Geo configuration takes effect and traffic begins flowing.
- Multi-Geo connectors aren't available through Quick Access.
- Multi-Geo supports only private enterprise apps.
- Multi-Geo doesn't support the Domain Name System (DNS) experience.
Source:


