GSA Internet Access + Web Content Filtering
Within GSA Internet Access, web category filtering gives administrators the ability to control access based on categories of websites or on specific domain names. Domains can be grouped into categories such as social media, gambling, or adult content, and rules can be created to allow or block traffic to those categories. The policies are linked to security profiles, which can then be applied through Baseline profiles and Conditional Access to specific users, groups, or devices.
The current release of web category filtering supports user- and context-aware controls based on fully qualified domain names and predefined categories. This provides a strong foundation for securing internet access in an identity-driven, easy-to-manage way.
In this post we will be focusing on setting up a blocklist of Alcohol And Tobacco web category aswell as the website adidas.com
Prerequisites
Be sure to have the following prepared before beginning
- Entra ID P1/P2, and Entra Suite or GSA Internet Access Addon license for the users
- Internet Access free trial 90-days: aka.ms/InternetAccessTrial
- Entra Suite free trial 90-days: aka.ms/EntraSuiteTrial
- Minimum the following roles
- Global Secure Access Administrator role to manage the Global Secure Access features.
- Conditional Access Administrator to create and interact with Conditional Access policies.
- Or Global Administrator which has "god mode" of the tenant
- You must disable Domain Name System (DNS) over HTTPS (Secure DNS) to tunnel network traffic. Use the rules of the fully qualified domain names (FQDNs) in the traffic forwarding profile. For more information, see Configure the DNS client to support DoH.
- Disable built-in DNS client on Chrome and Microsoft Edge.
- IPv6 traffic isn't acquired by the client and is therefore transferred directly to the network. To enable all relevant traffic to be tunneled, set the network adapter properties to IPv4 preferred.
- User Datagram Protocol (UDP) traffic (that is, QUIC) isn't supported in the current preview of Internet Access. Most websites support fallback to Transmission Control Protocol (TCP) when QUIC can't be established. For an improved user experience, you can deploy a Windows Firewall rule that blocks outbound UDP 443:
@New-NetFirewallRule -DisplayName "Block QUIC" -Direction Outbound -Action Block -Protocol UDP -RemotePort 443. - Check out the list of GSA Points of Presence to see which service edge is closest to you https://learn.microsoft.com/en-us/entra/global-secure-access/reference-points-of-presence
- Entra ID-Joined machines
Setup GSA Traffic Forwarding
The Internet Access traffic forwarding profile directs internet traffic through the Global Secure Access client. When enabled, this profile ensures that remote users connect to the internet in a secure and controlled manner. With Microsoft Entra Internet Access, you gain the ability to define which websites can be accessed, while also having the flexibility to exclude specific traffic from Global Secure Access based on IP addresses, ranges, subnets, or Fully Qualified Domain Names (FQDNs).
- Browse entra.microsoft.com
- Scroll down to Global Secure Access -> Settings -> Session Management.
- Click the tab Adaptive Access and toggle: Enable CA Signaling for Entra ID (covering all cloud apps)
Global Secure Access signaling provides network location information to Conditional Access, enabling admins to create policies that restrict user access to specific apps based on their use of the Global Secure Access client or a remote network
Now let's enable Internet Access Profile
- In Entra Portal, click on Global Secure Access -> Connect -> Traffic forwarding
- Toggle Internet access Profile
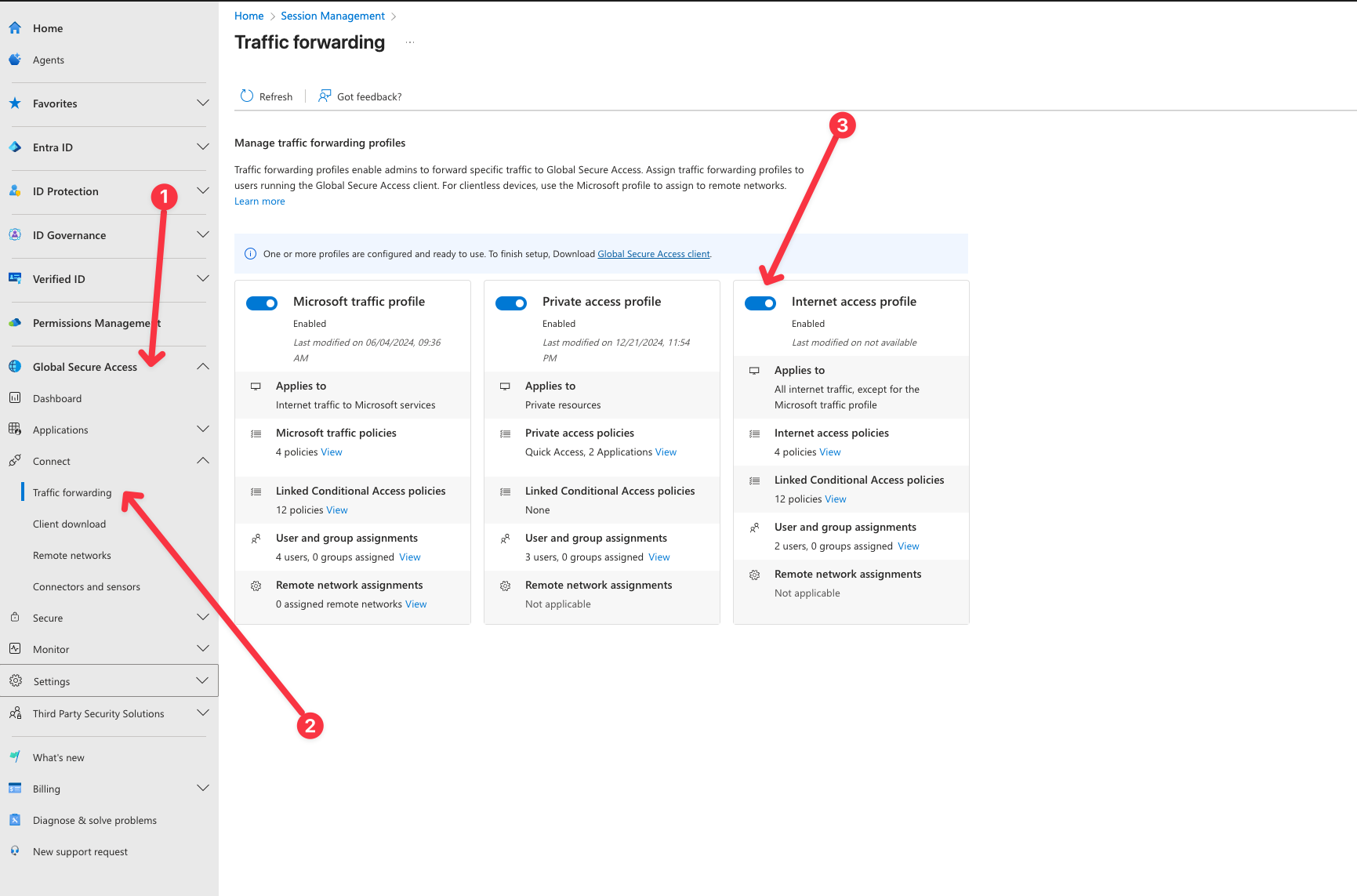
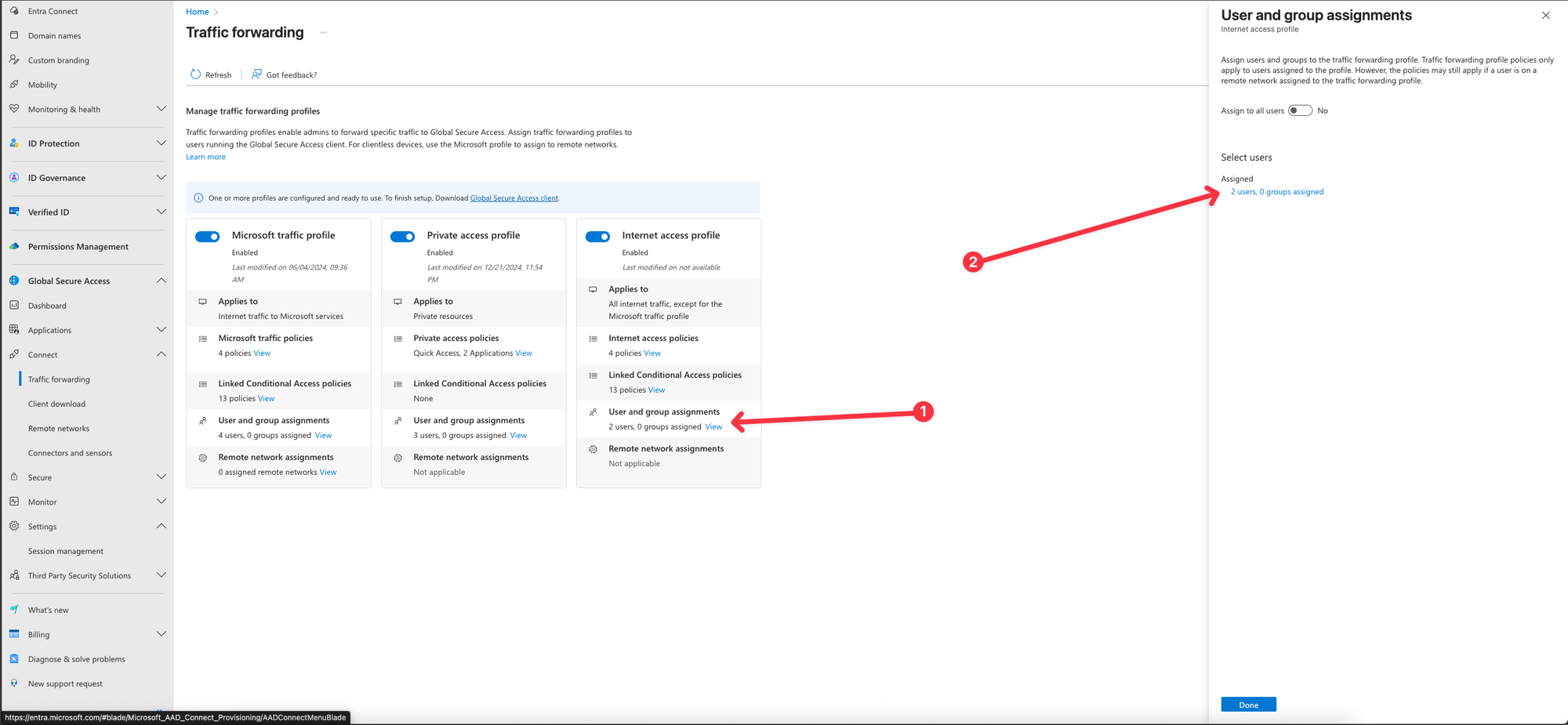
- Assign the users and/or groups which should be targeted
Create a web content filtering policy
Web content filtering enables organizations to enforce granular Internet access controls by categorizing websites and applying appropriate restrictions.
The initial Secure Web Gateway (SWG) capabilities in Microsoft Entra Internet Access include domain-based web content filtering. These filtering policies are seamlessly integrated with Microsoft Entra ID and Microsoft Entra Conditional Access, providing user-aware and context-aware controls that are straightforward to configure and manage.
At present, the web filtering functionality is limited to Fully Qualified Domain Name (FQDN)-based filtering, supporting both web category filtering and direct FQDN filtering
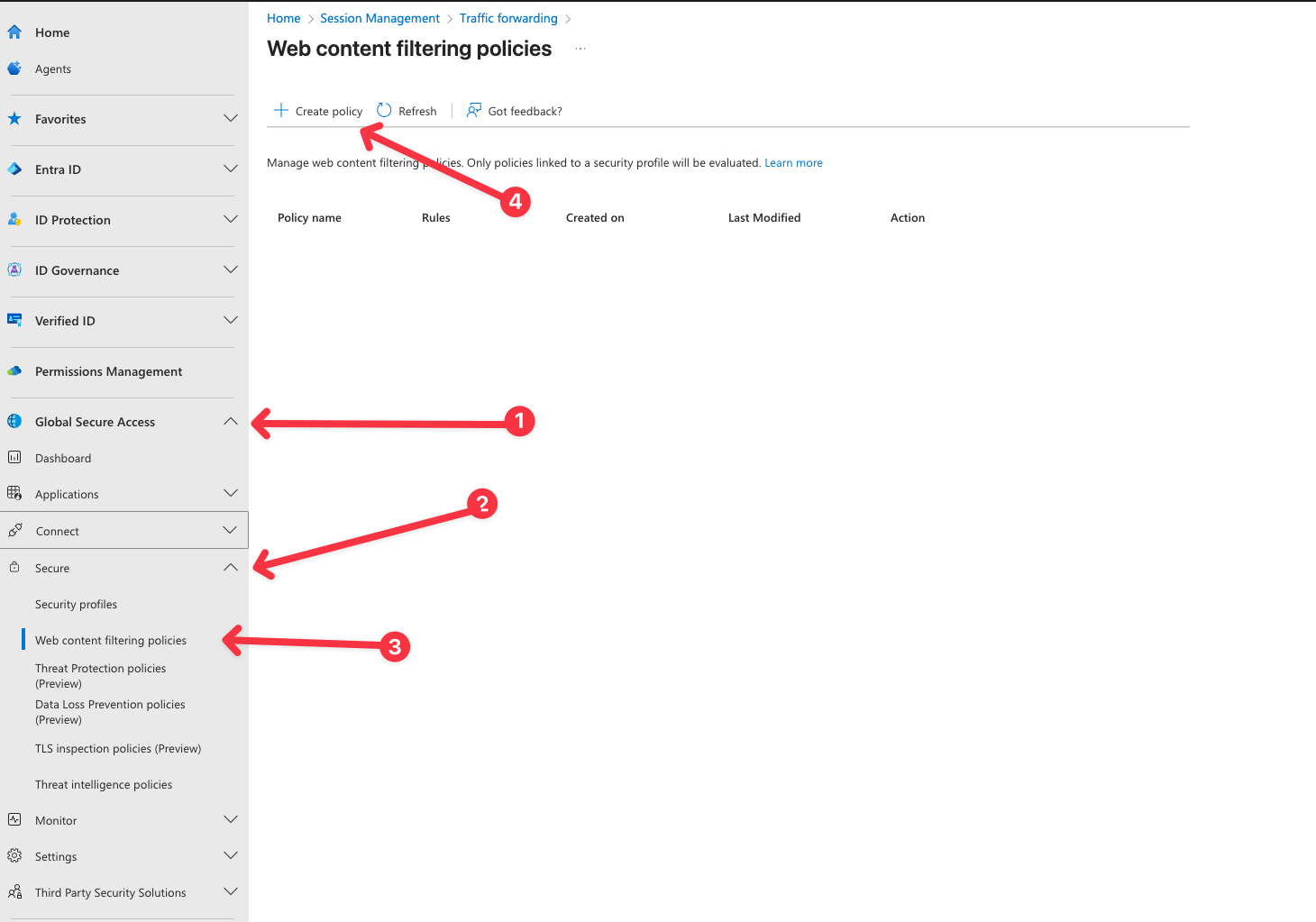
- In Entra Portal, Browse to Global Secure Access -> Secure -> web content filtering policy.
- Select Create policy.
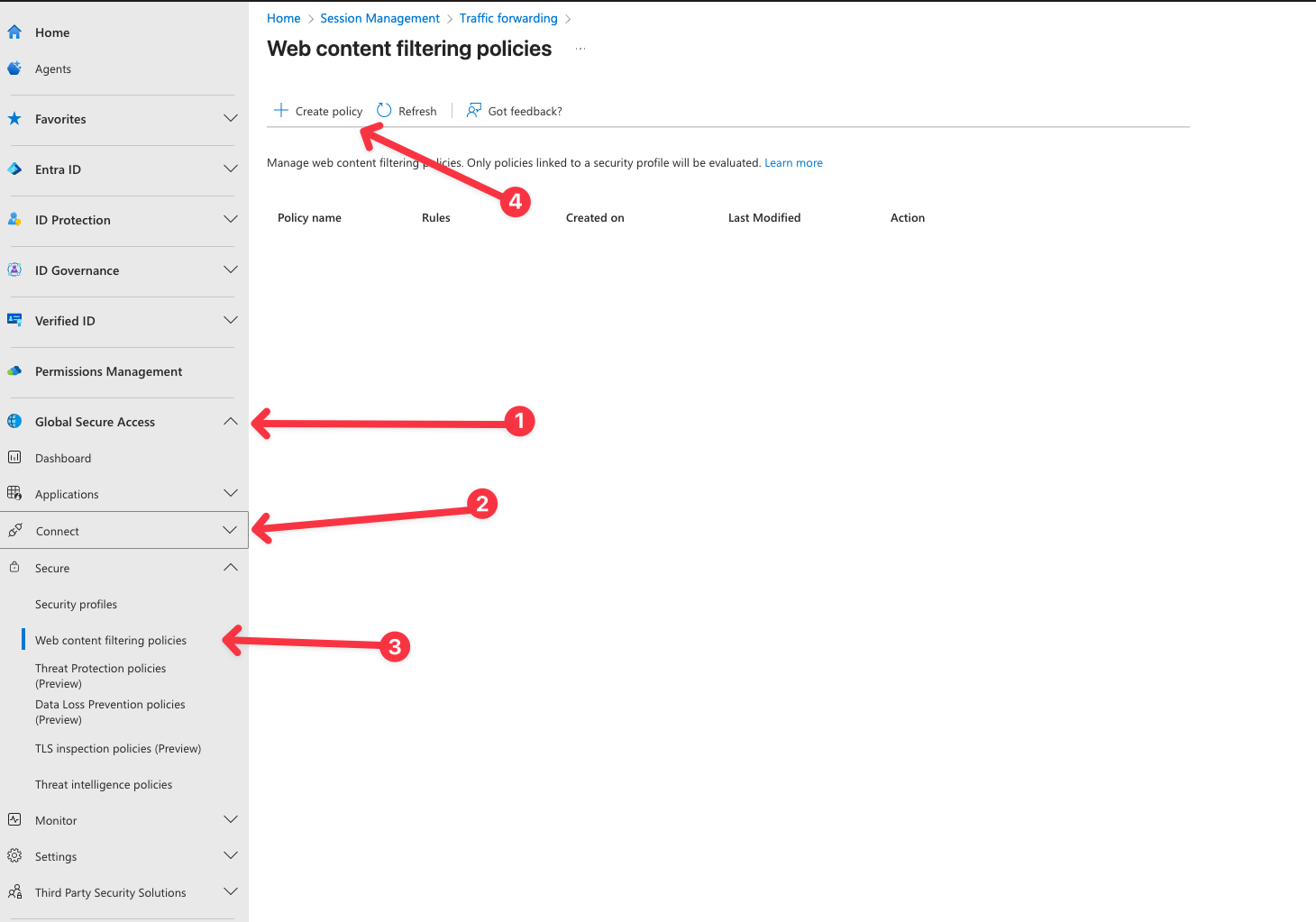
- Click Next
- Give the policy a name and set the action to Block. Add a description if you want to
- Name: Alcohol And Tobacco
- Action: Block
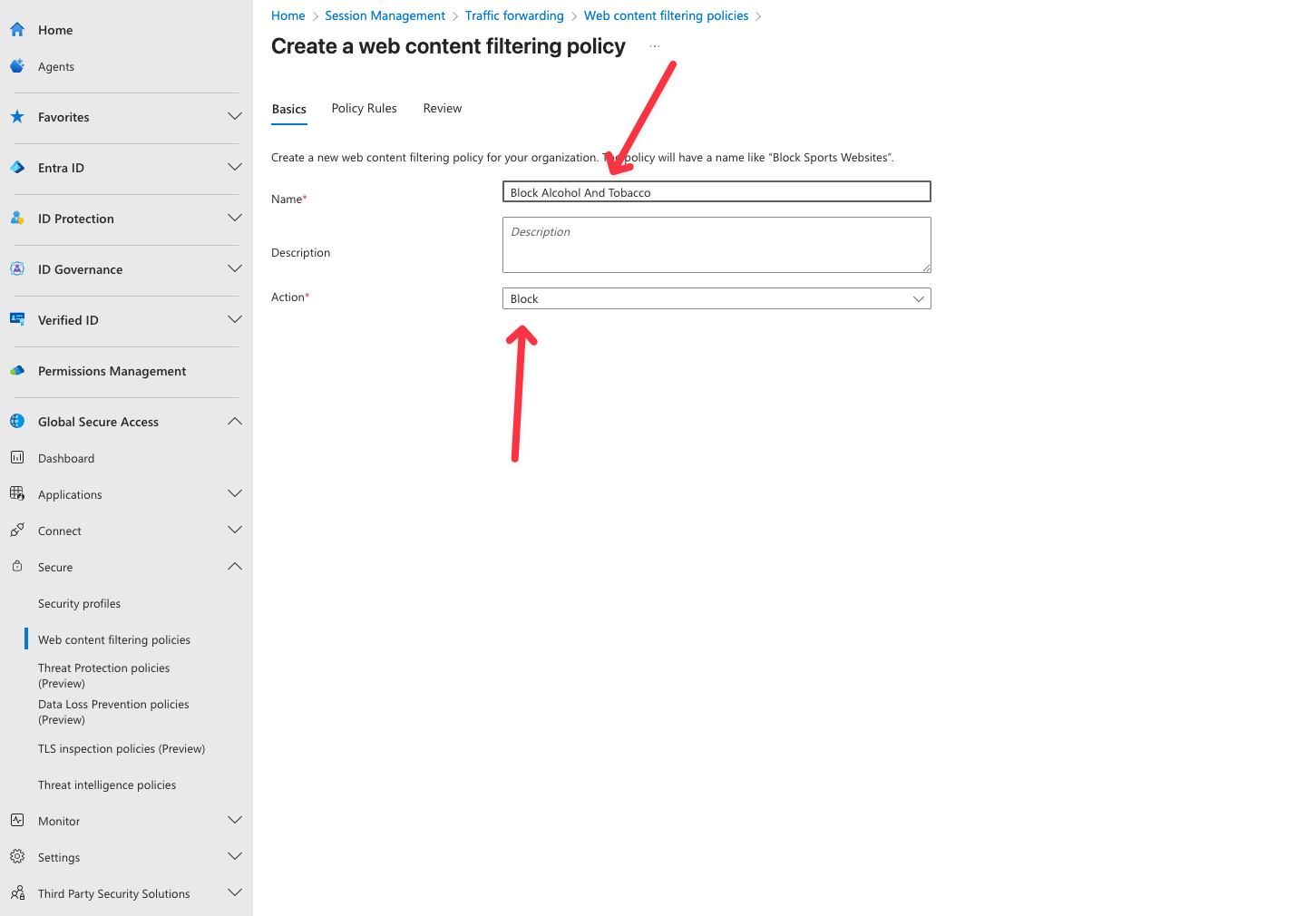
- Click Next
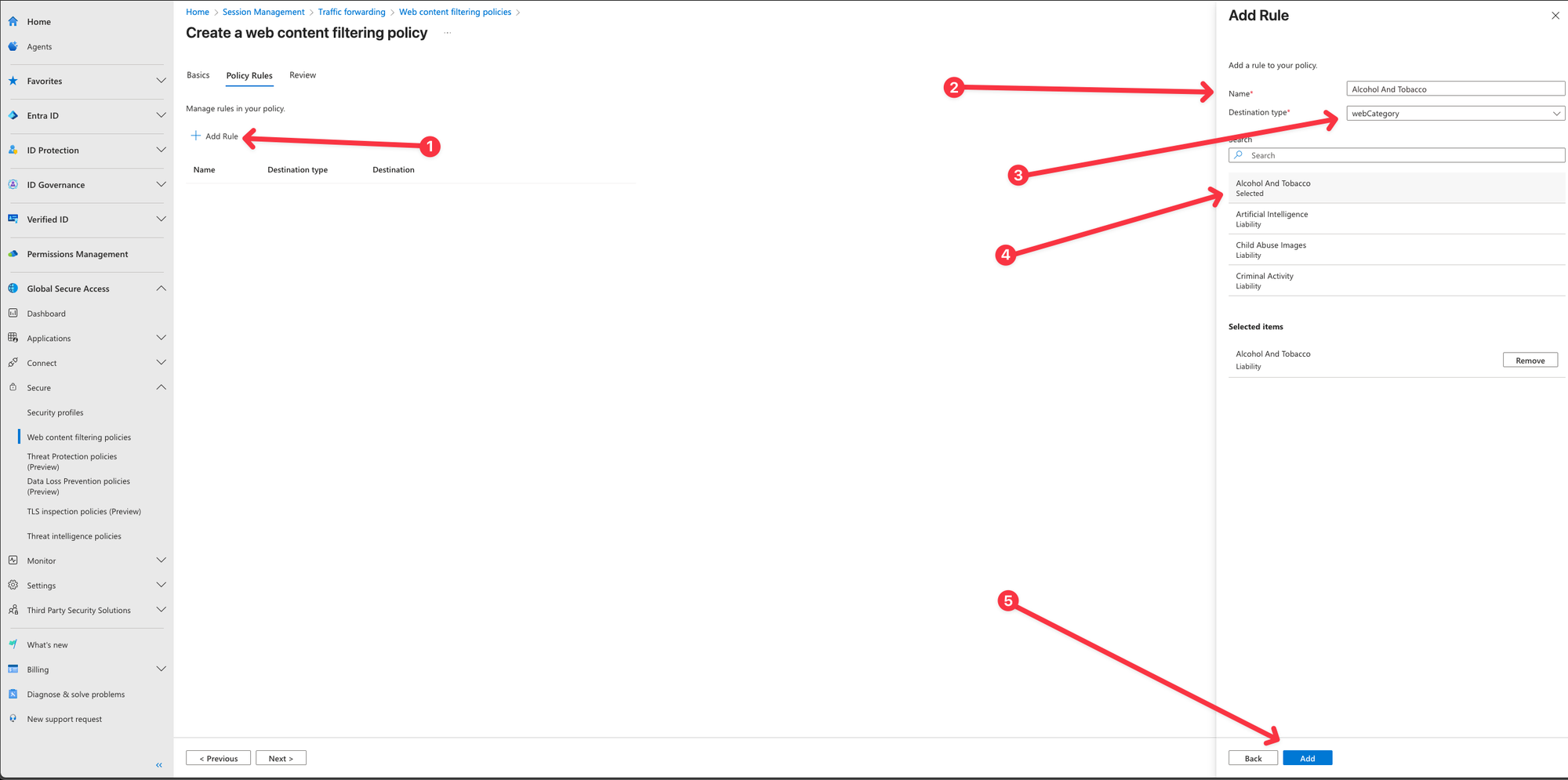
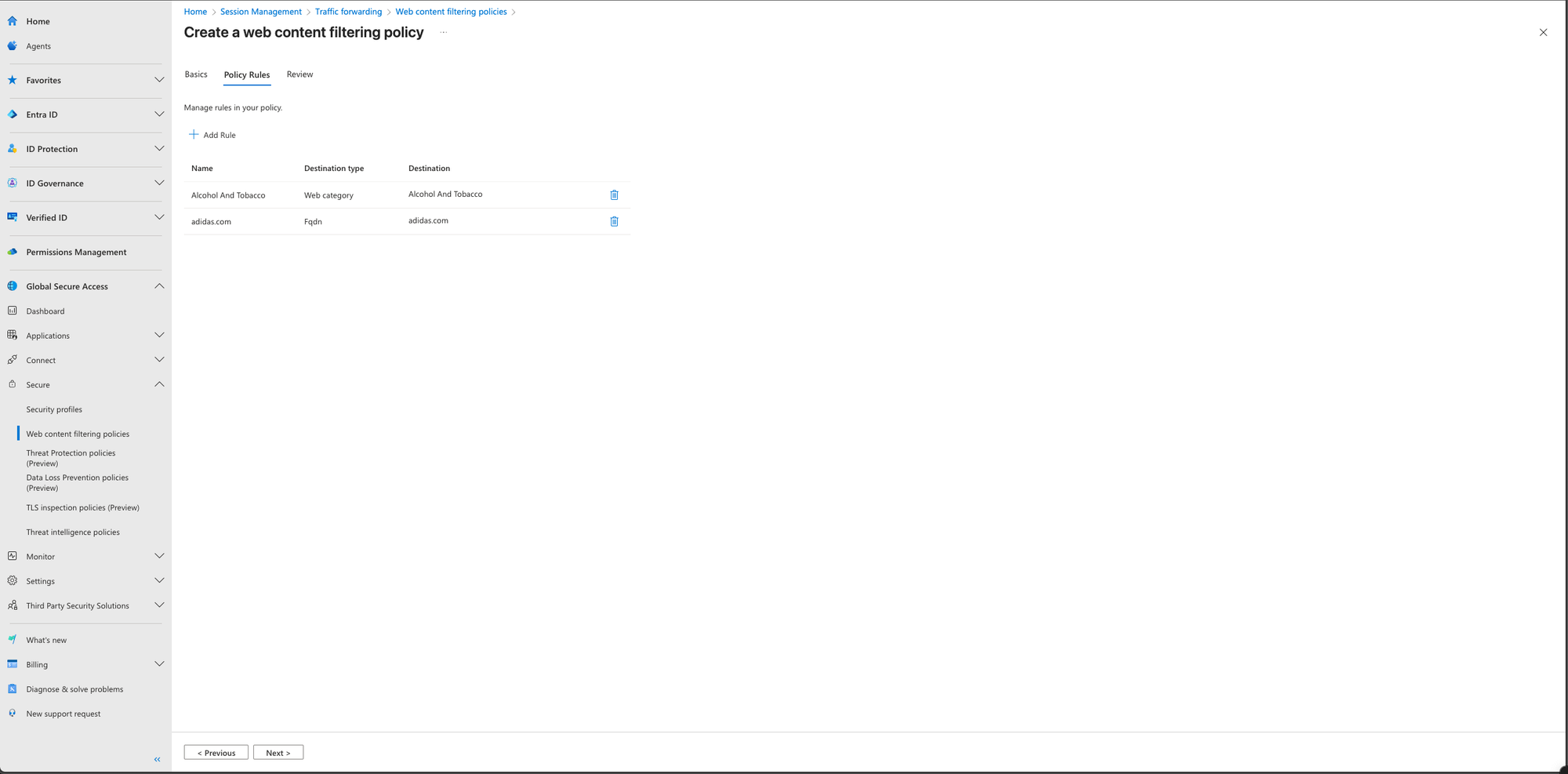
Click on Add rule and give the rule a name, on the Destination type pick webCategory and select Alcohol And Tobacco, when done click on Add
- Repeat the steps for Add rule, and change the Destination type to fqdn, type in adidas.com and press Add
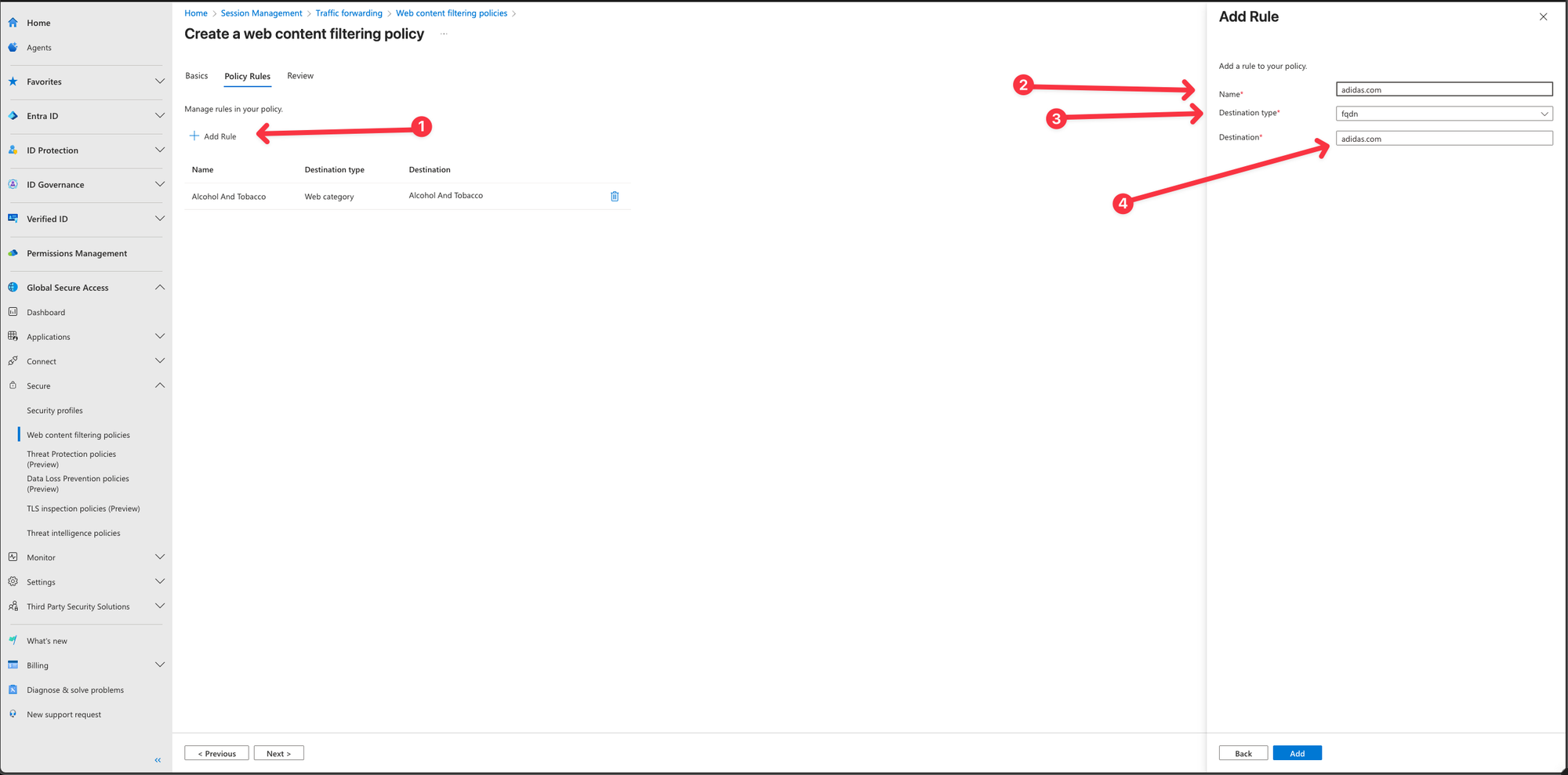
We now have a Web Content filtering policy consisting of 2 rules, which blocks the web category Alcohol And Tobacco and the website adidas.com
- Click on Next and create the Policy
Create a security profile
Security profiles are a grouping of filtering policies. You can assign, or link, security profiles with Microsoft Entra Conditional Access policies. One security profile can contain multiple filtering policies. And one security profile can be associated with multiple Conditional Access policies.
In this step, you create a security profile to group filtering policies. Then you assign, or link, the security profiles with a Conditional Access policy to make them user or context aware.
- In Entra Portal, Browse to Global Secure Access -> Secure -> Security profiles
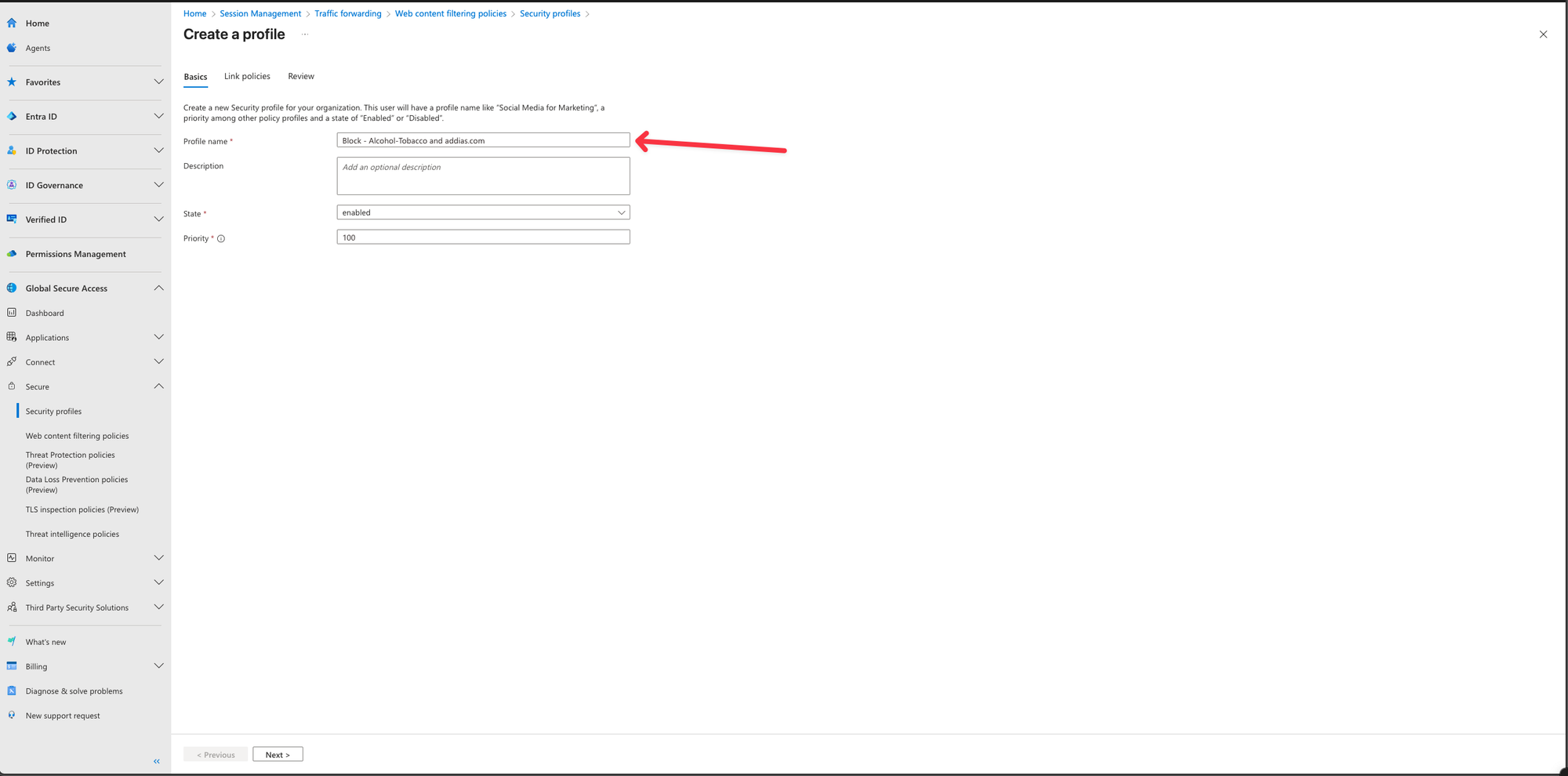
- Select Create profile.
- Enter a name and description for the policy and select Next.
- Leave the Priority on 100
- Click Next
- Select Link a policy and then select Existing web filtering policy. Select the Policy we have created and click Add
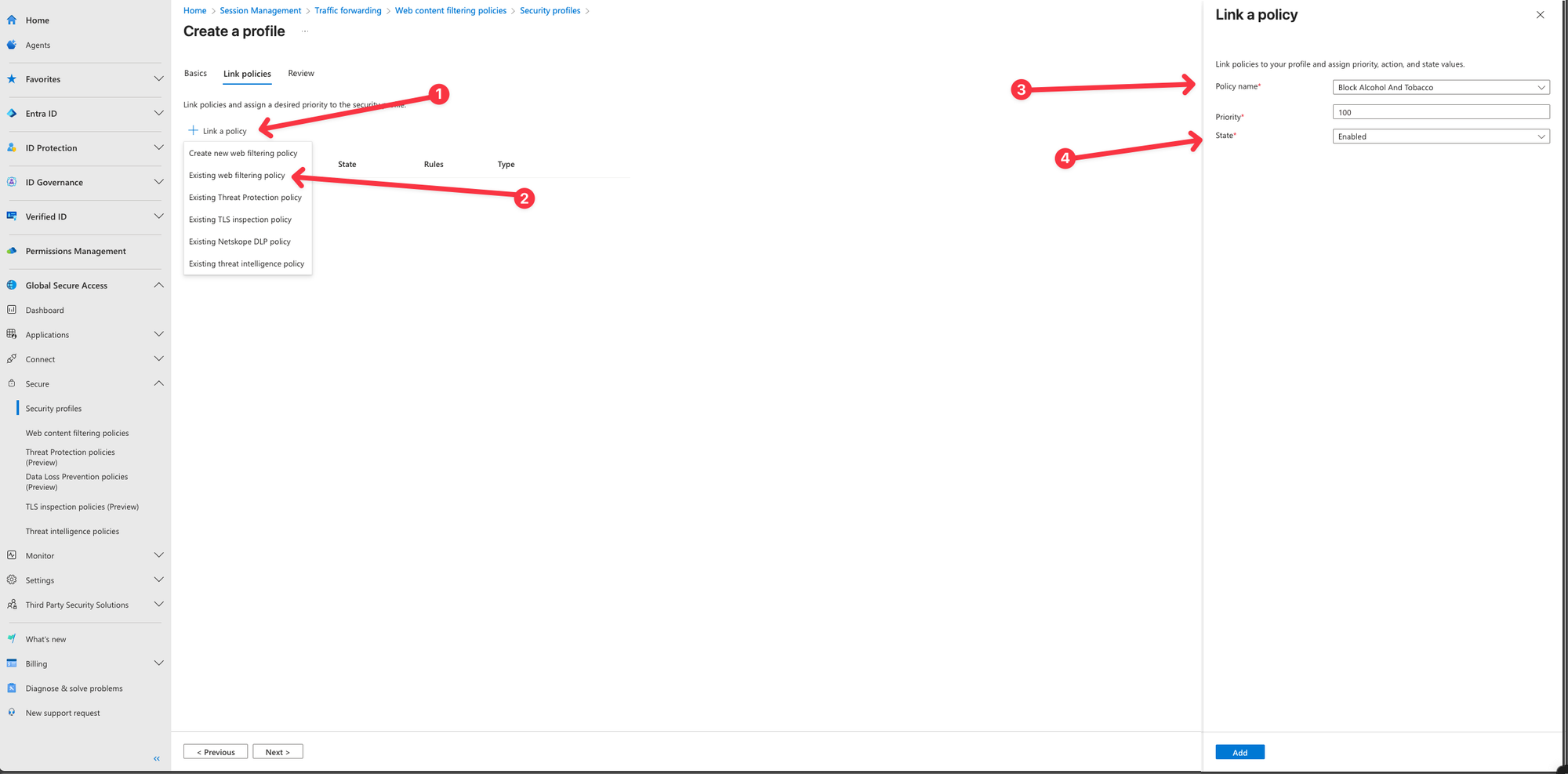
- Click Next and create the Security Profile
Create and link Conditional Access policy
Create a Conditional Access policy for end users or groups and deliver your security profile through Conditional Access Session controls. Conditional Access is the delivery mechanism for user and context awareness for Internet Access policies. To learn more about session controls, see Conditional Access: Session.
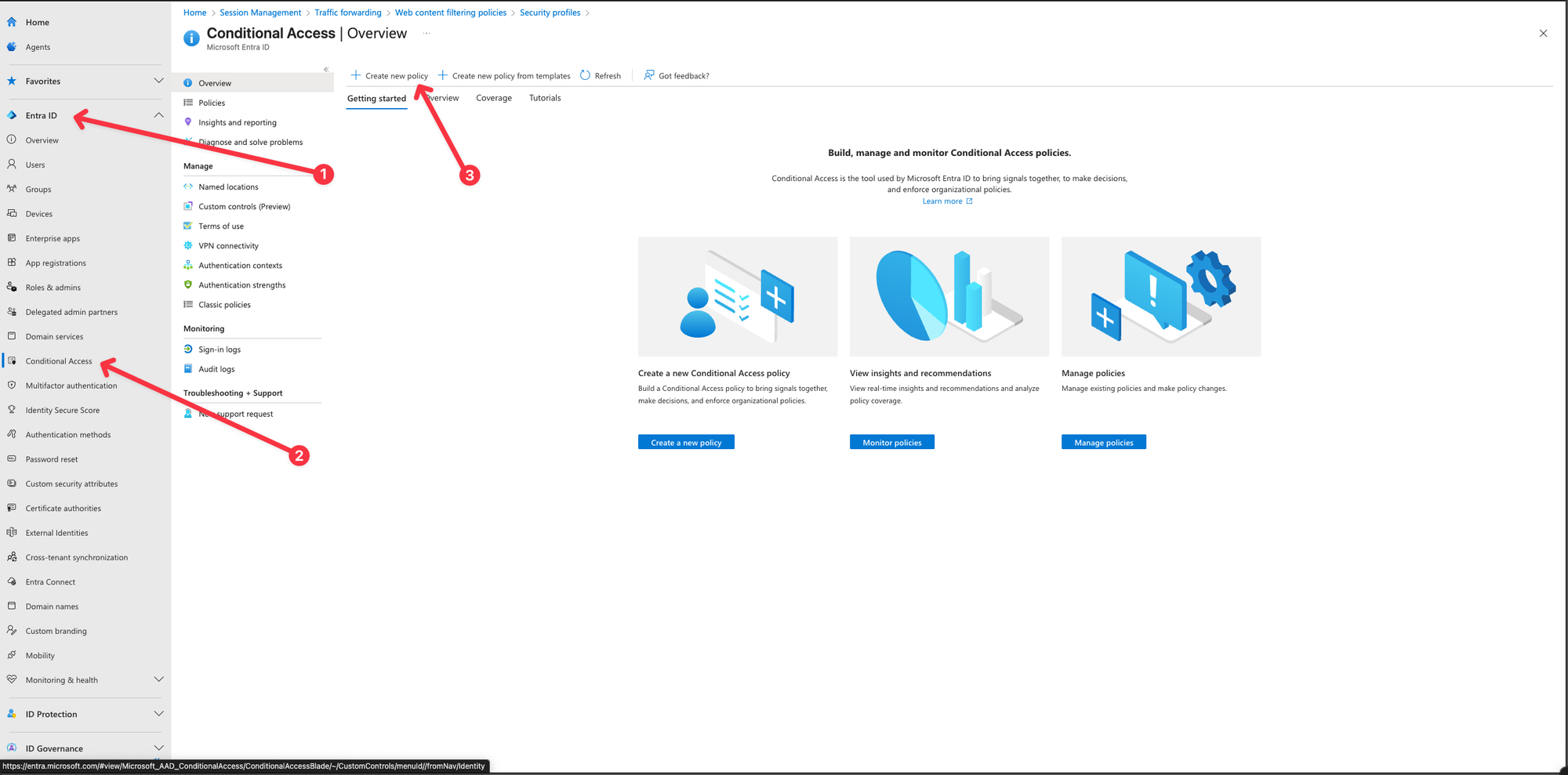
- In Entra Portal, Browse to Entra ID -> Conditional Access.
- Select Create new policy.
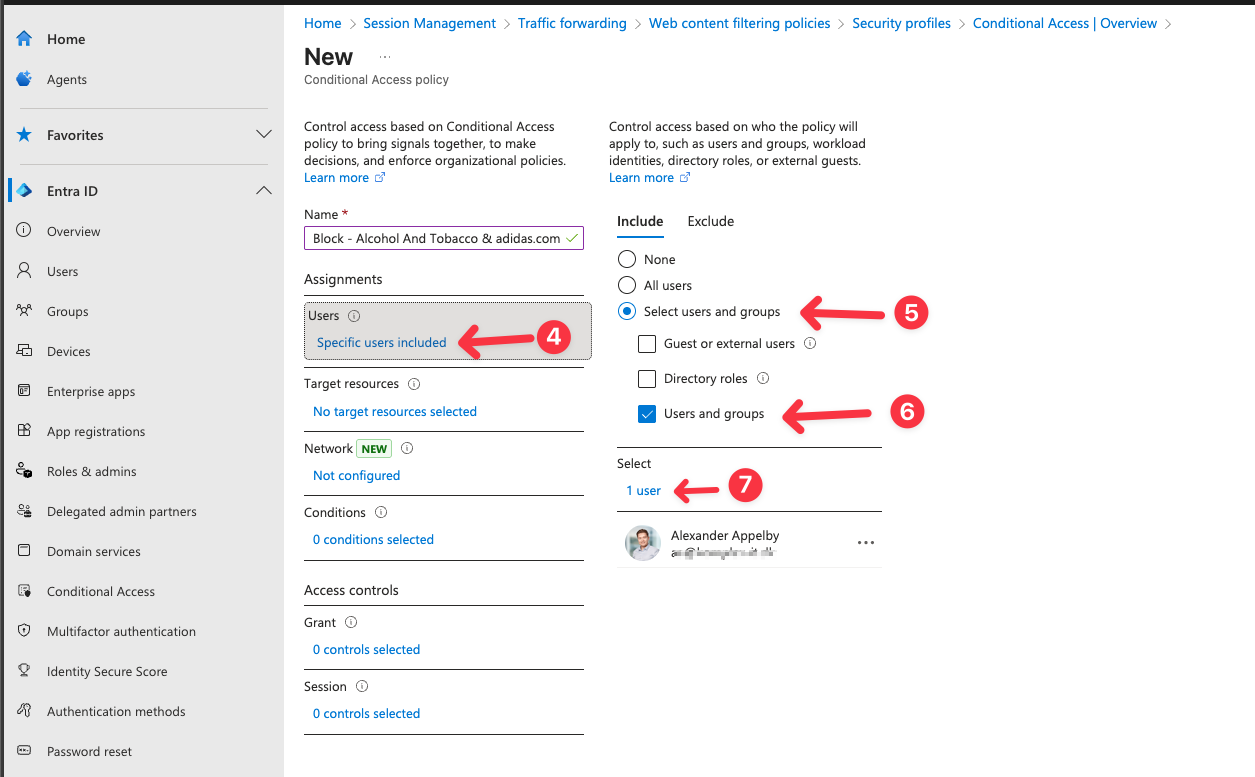
- Enter a name and assign a user or group.
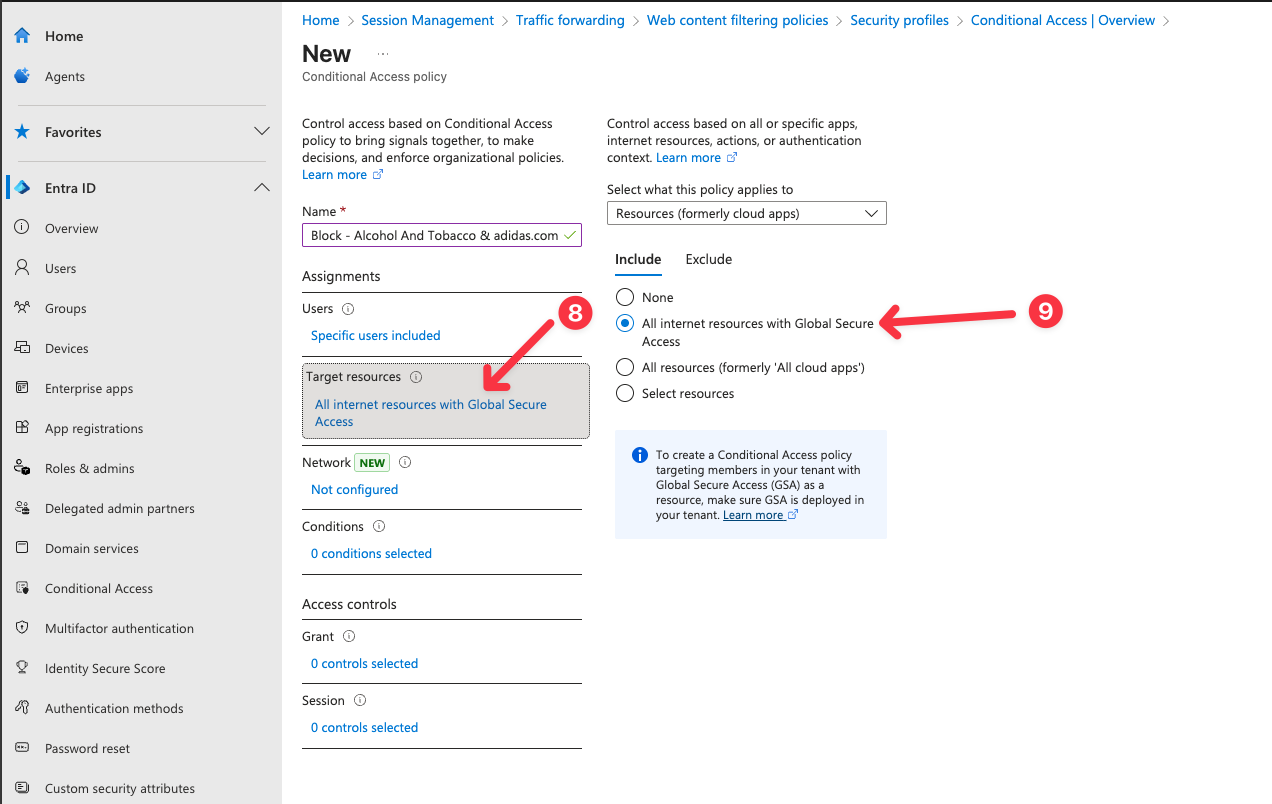
- Select Target resources and All internet resources with Global Secure Access.
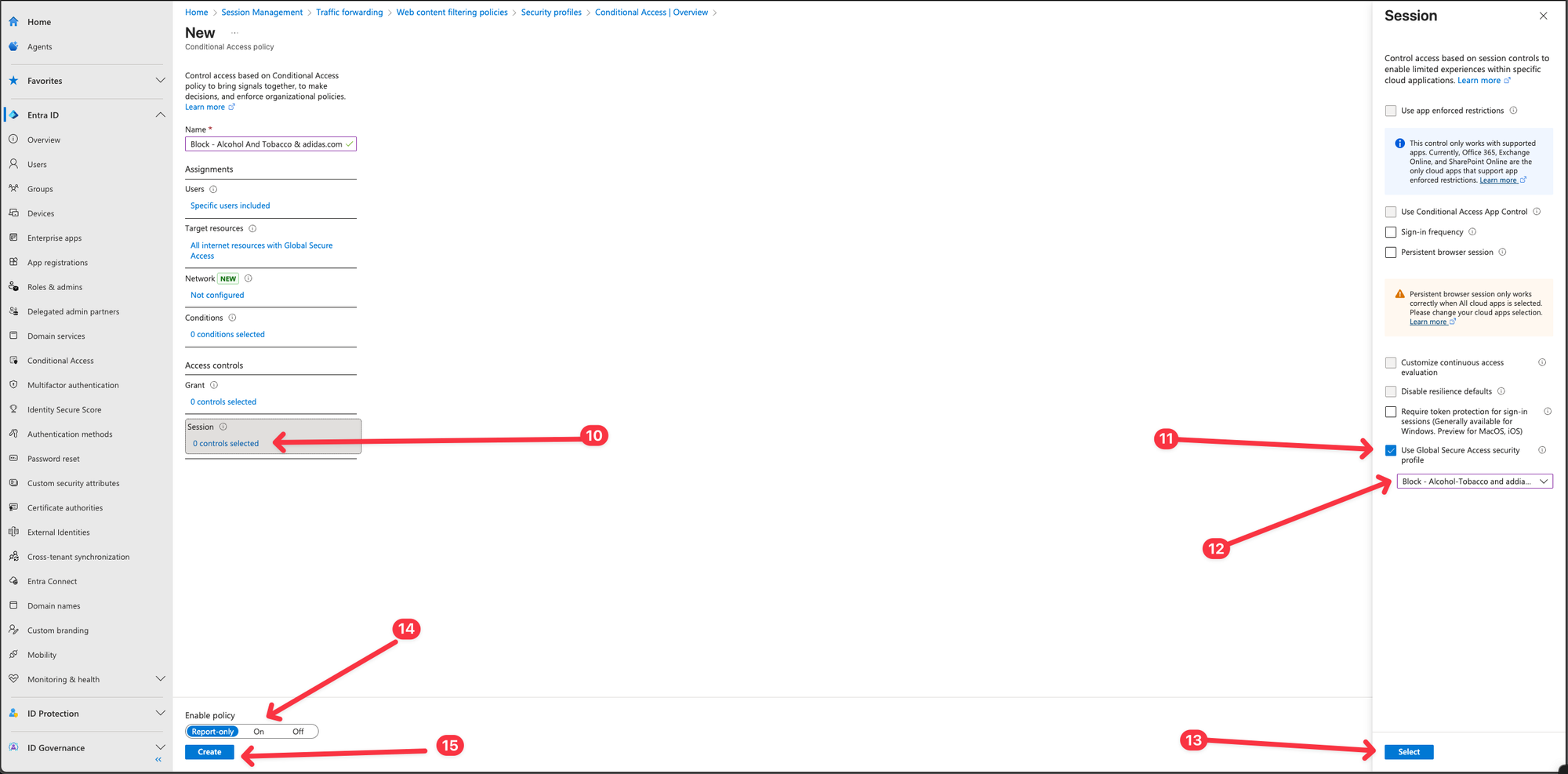
- Select Session -> Use Global Secure Access security profile and choose a security profile.
- Select Select.
- Toggle Enable Policy to On and click Create
Verify outcome of the policy
Ensure that your users have the Global Secure Access Client installed on their endpoints.
The client is supported on:
- Windows 10 / 11
- Windows on ARM (Preview)
- macOS
- Android
- iOS (Preview)
Additionally, the client must be Entra ID–joined.
Download the Client from the Entra ID Portal or deploy it to the through Intune
- In Entra Portal, Browse to Global Secure Access -> Connect -> Client download
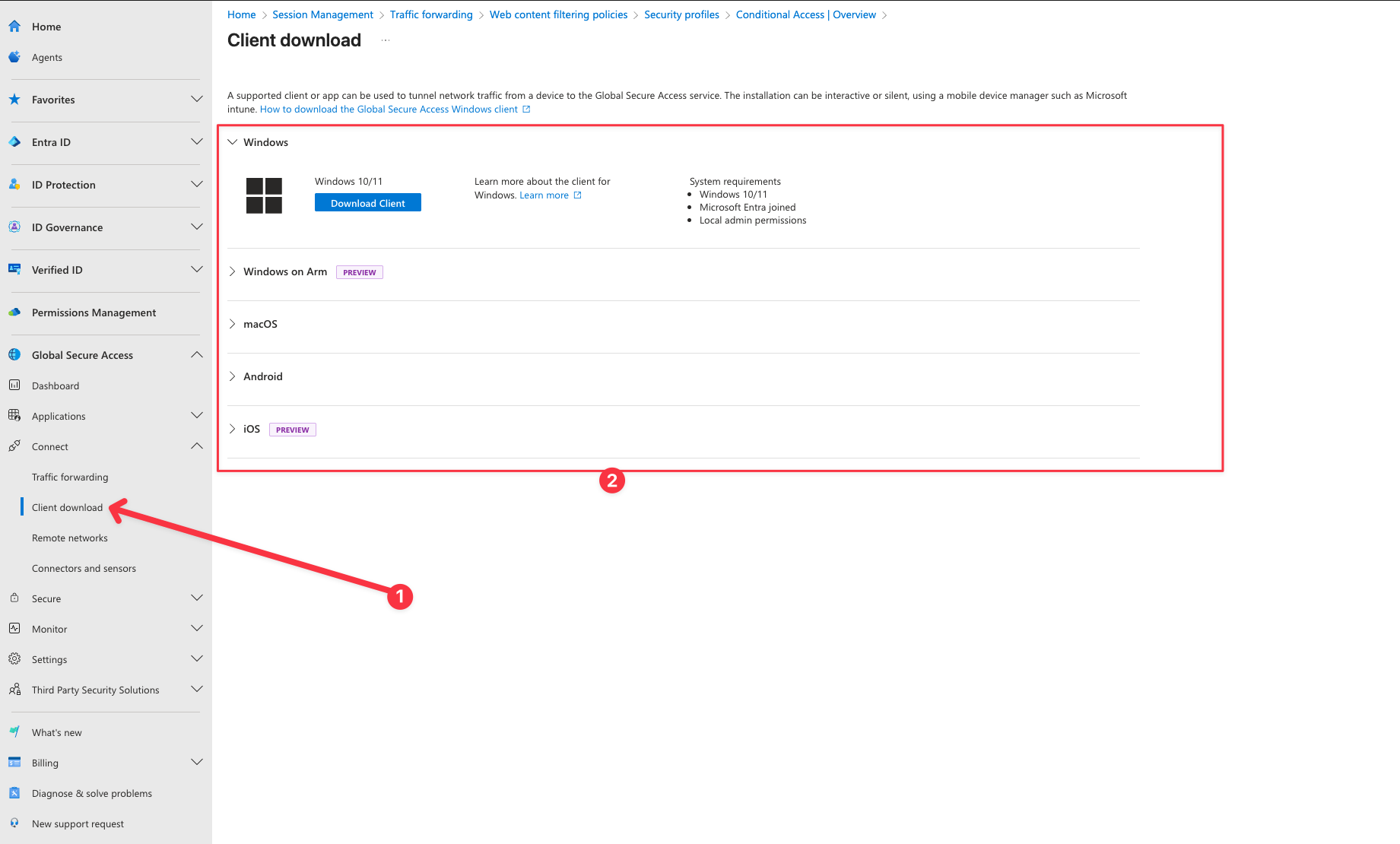
After the GSA Client has been successfully installed, the Internet channel should become visible and display a green check mark to indicate proper functionality.
- Open the GSA client from taskbar
- Verify the Internet channel is active
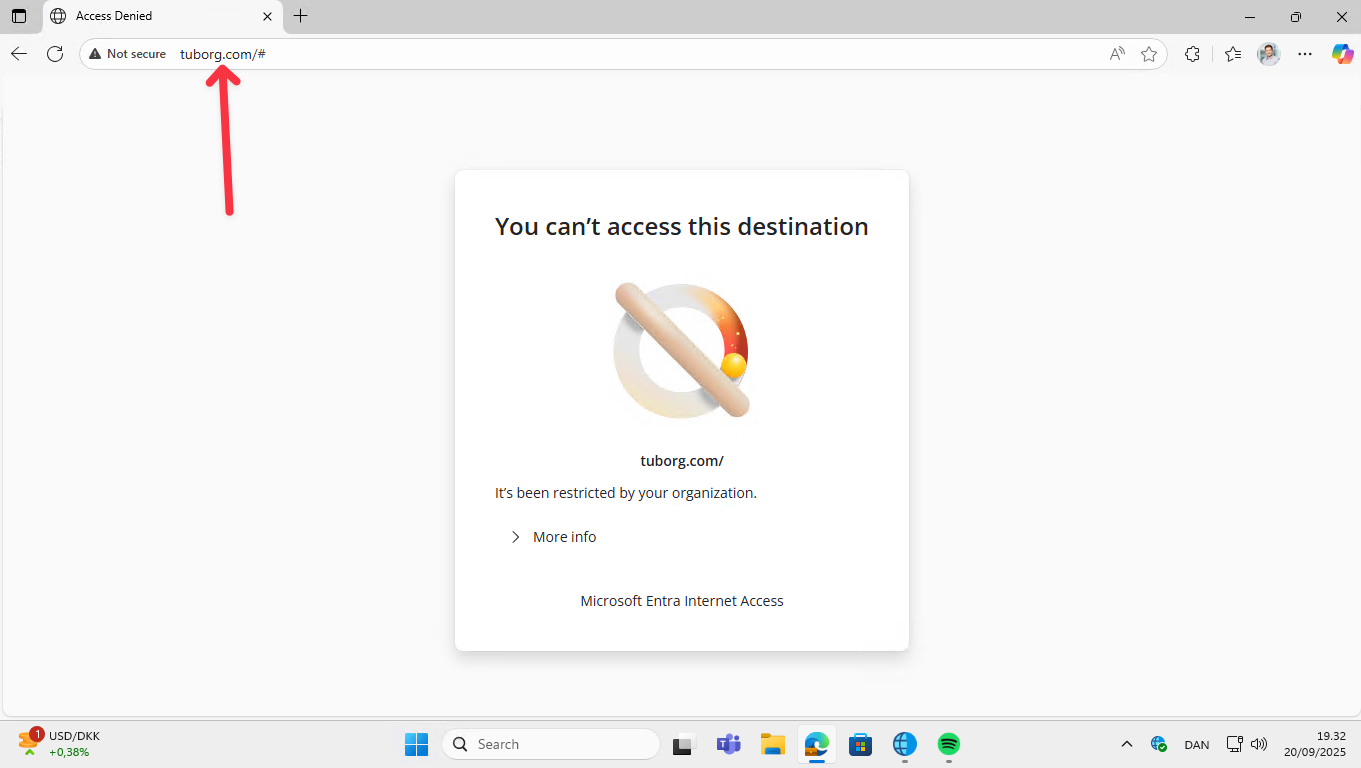
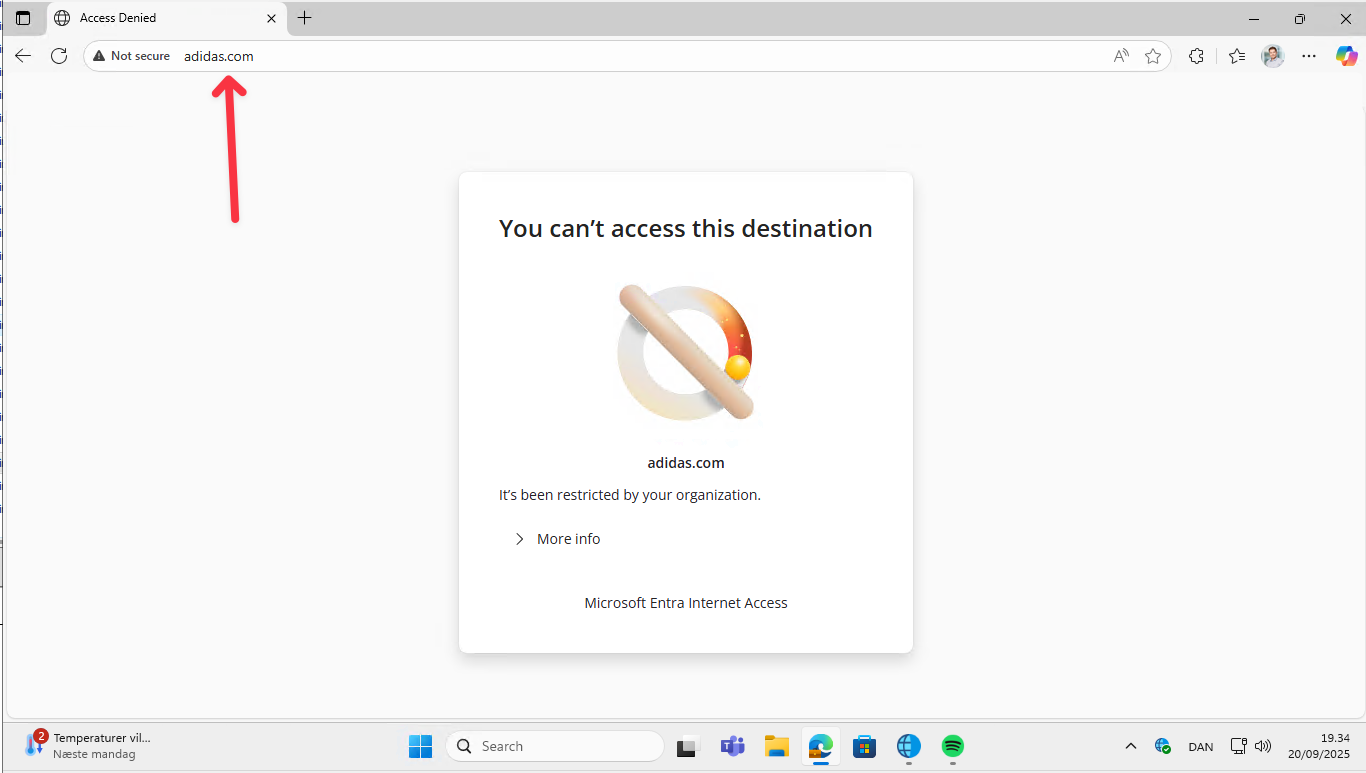
Next, navigate to a website that contains alcohol or tobacco related content. In this example, I will be browsing tuborg.com. Additionally, I will also visit adidas.com for testing purposes.
If configured correctly, access to the websites should be blocked.
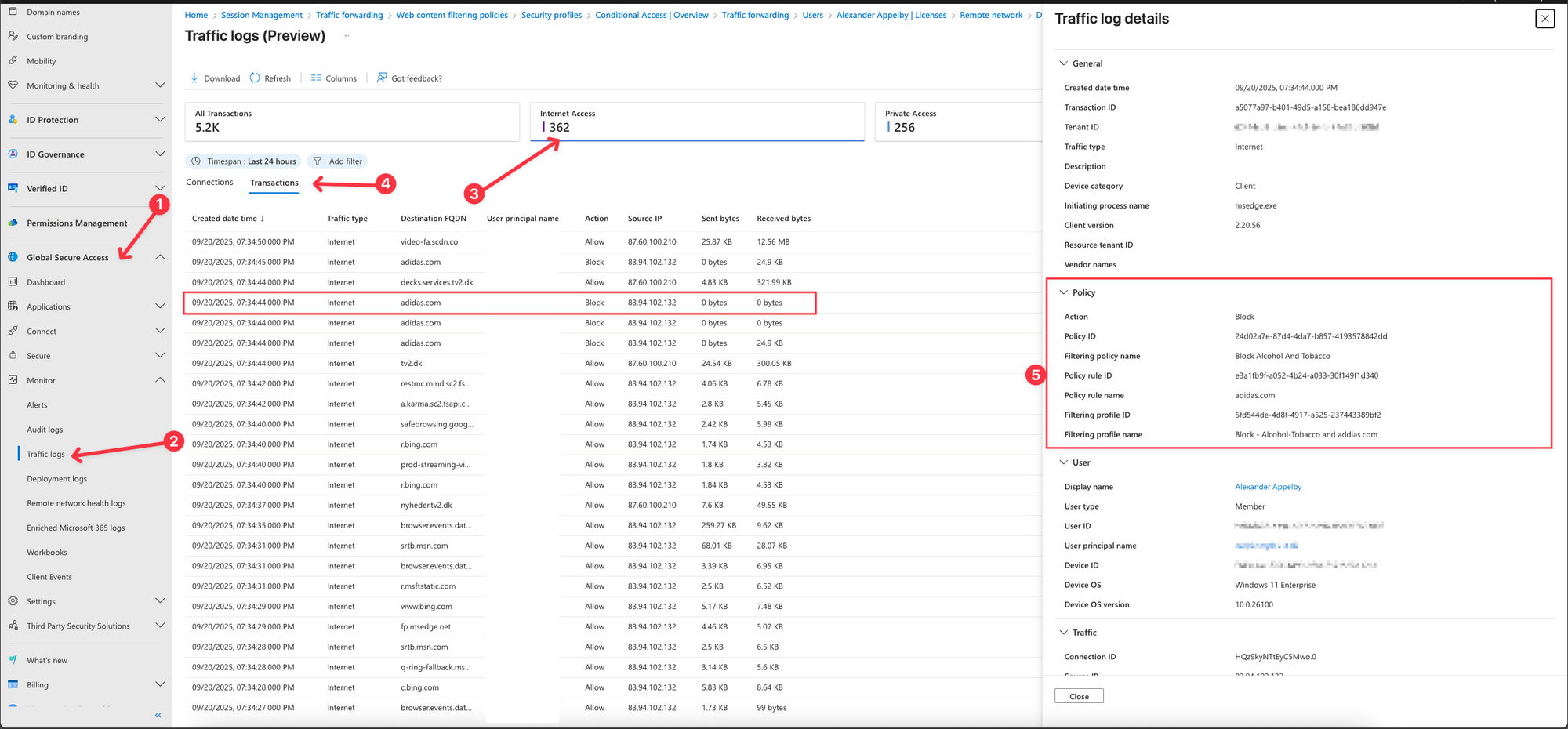
Let’s review the Traffic logs in the Entra portal and examine the corresponding Transaction logs.
- In Entra portal, Browse to Global Secure Access -> Monitor -> Traffic logs
- Click on Internet Access then Transactions.
- Select a blocked transaction, in this case, I have chosen the transaction from adidas.com.
We can confirm that the Policy Block - Alcohol-Tobacco and addidas.com was triggered, resulting in the website adidas.com being blocked for the user.
What category is a website in?
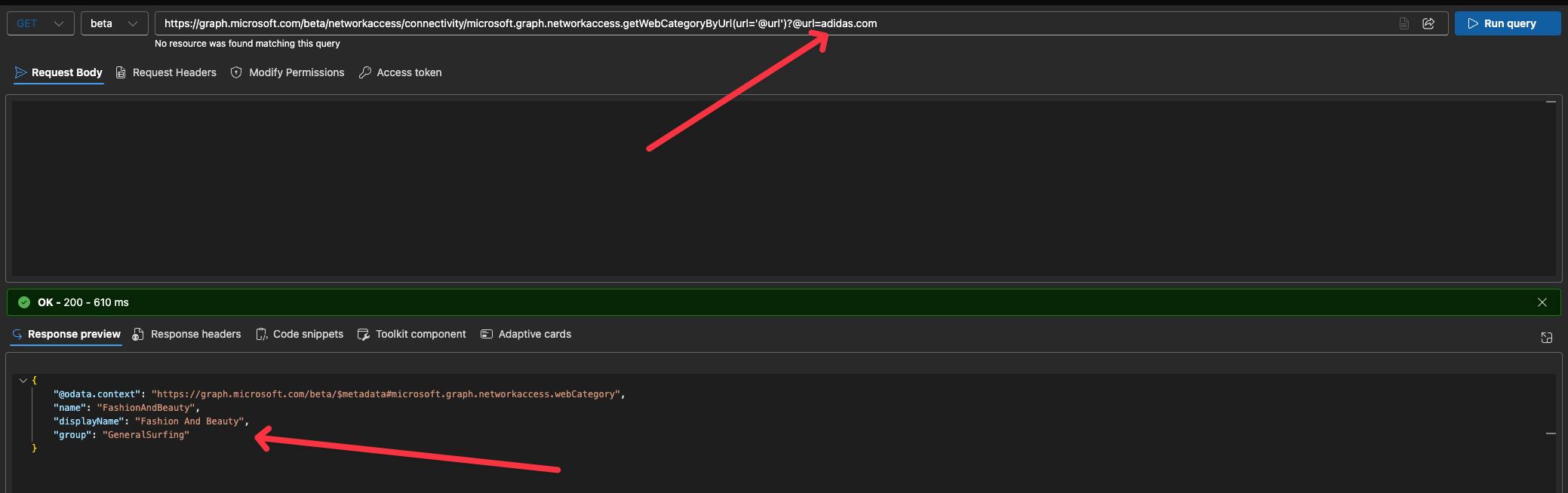
If you are unsure of how a specific website is categorized, you can use the Microsoft Graph API to perform a lookup on the URL. This will return detailed information about the web category in which the given URL has been placed, allowing you to better understand and verify its classification.
- Sign in to Graph Explorer at https://aka.ms/ge as atleast a Global Secure Access Administrator.
- Set the HTTP method to GET and the API version to beta
Run this query, and replace example.com with the URL you wish to check
GET https://graph.microsoft.com/beta/networkaccess/connectivity/microsoft.graph.networkaccess.getWebCategoryByUrl(url='@url')?@url=example.com
Below picture shows that Adidas.com, is placed in the Fashion And Beauty Web Category